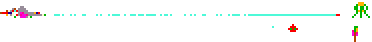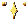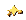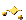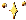Translate this!
- Tunnelcat
- DBB Grand Master

- Posts: 13310
- Joined: Sat Mar 24, 2007 12:32 pm
- Location: Pacific Northwest, U.S.A.
Translate this!
Challenge! Who can translate what this says without any hints. If you're a geek, you should be able to figure this one out. 


-
Valin Halcyon
- DBB Admiral

- Posts: 1113
- Joined: Sun Jan 02, 2000 3:01 am
You really need to try harder. Symbol replacement ciphers are ridiculously easy to solve. Took me about 30-40 minutes. Fourth word was my key:
Keep out of reach of
children under the
age of five hundred.
For best results,
sacrifice a small
mammal xanroc,
then apply evenly to
interior of eyeball.
Would you like to
sell Dr. Flimflam
products, contact a
representative at a
covered wagon near
you.
That said...I haven't a clue if those symbols came from anywhere. Never saw them before in my life. And what the hell is a xanroc?
Keep out of reach of
children under the
age of five hundred.
For best results,
sacrifice a small
mammal xanroc,
then apply evenly to
interior of eyeball.
Would you like to
sell Dr. Flimflam
products, contact a
representative at a
covered wagon near
you.
That said...I haven't a clue if those symbols came from anywhere. Never saw them before in my life. And what the hell is a xanroc?
- Tunnelcat
- DBB Grand Master

- Posts: 13310
- Joined: Sat Mar 24, 2007 12:32 pm
- Location: Pacific Northwest, U.S.A.
Well sheeesh, I should have known a cryptographer was part of this community! You got the translation correct. Congrats, you win a Kewpie Doll!
Thanks Grendal for the link to the AL2 language. It was referenced in the extras of the DVD 'Bender's Big Score', but I couldn't find out how it was different from the AL1 version.
I typed up the label in Word and created the JPEG image in my original post because the screenshot was too blurry to read. This is what the label looked like in Futurama.

It was referenced in this episode:
'Less Than Hero' 2003
Here's a link if anybody wants to download the AL1 font into MS WORD:
http://www.futurama-madhouse.com.ar/fonts/index.shtml
Thanks Grendal for the link to the AL2 language. It was referenced in the extras of the DVD 'Bender's Big Score', but I couldn't find out how it was different from the AL1 version.
I typed up the label in Word and created the JPEG image in my original post because the screenshot was too blurry to read. This is what the label looked like in Futurama.

It was referenced in this episode:
'Less Than Hero' 2003
Here's a link if anybody wants to download the AL1 font into MS WORD:
http://www.futurama-madhouse.com.ar/fonts/index.shtml
-
Valin Halcyon
- DBB Admiral

- Posts: 1113
- Joined: Sun Jan 02, 2000 3:01 am
How about something cryptographic that isn't a cipher? I'll even throw in some historical relevance.
In the 1940s, Soviet spies in the United States corresponded with Moscow using a cryptographic system known as a One Time Pad. OTP is literally the perfect code--completely unbreakable. Most codes are just \"excessively difficult, but with enough computers, it could be done\" unbreakable. OTP is literally unbreakable; if you follow its rules perfectly, then millenia from now, regaurdless of advances in cryptography and computing, a message you encode in OTP will still be unreadable.
The system is simple. You and your partner are equipped in advance with a pad of sheets of completely random numbers -- and these two pads are identical. When you need to send a message, you start by encoding your message in a standard cipher -- A=1, B=2, and so forth. You then take a sheet from your pad, and add the series random numbers to the message, doing all arithmetic mod 26. This you transmit, and your partner decrypts by using his copy of the sheet and subtracting off the random numbers. Then you both burn that sheet and never use it again. Thus \"One Time\" pad. (Actually, this is a simplification that isn't as secure--but it illustrates the point; for this exercise, it'll do).
Why is the \"one time\" part important? Well, it turns out that if you use the sequence twice, the messages are relatively easy to crack, though certainly harder than a symbol cipher. And as it historically turns out, the Soviets did exactly that. Their system was a little different than I described (they translated whole words to numbers instead of using a cipher), but it was perfectly secure from a cryptographic perspective. But apparently, Russian manufacturing being what it was, some of the pads were duplicated, and that means . . . used twice.
The United States's Project VENONA took advantage of the mistake, successfully decrypting many messages between KGB agents abroad and Moscow.
Can you solve the same problem?
The following two messages have been encoded with a Two Time Pad. It was supposed to be a One Time Pad, but the cipher was used twice. Of course, you won't be able to read the end of the longer message -- but if you're able to read any of either message at all, you'll know why. I've left the spaces and punctuation unchanged. The alphanumerics are rotated according to a series of random* numbers, arithemetic done mod 26.
* I used dice. So don't be tryin' to attack my pseudorandom number generator.
For fun, I've used messages actually decoded through Venona as the cleartext. In the 40's, this stuff was Top Secret.
---- First message ----
Uvxi: Xzj Lclbmhnmy
Mp: Chwxvr
5 Xyox., 1944
Lp Hqdohh,
KCVFGWXXN roubxa znfg Psginsxd sq wol sdgaxxnym IWABWLKGKB rn 31vl Dgxddf. Zu ael nnmrnys, fautprx ysb kphqk.
PGJS
---- Second message ----
Uvxi: Rnoizh
Hy: Ljxdxwywij
8 Zzun., 1944
Slwsq qt oau iprgneyw ge cdwtkcvzhg vtakslli frclr lgfzwk jeu ujoxja nebo flfdztn Ldkonn. Plqm Okpgmd ua ii gejdmvzabbjs bjwskdehcxod fm use qhvfxy scmq am Jwqguskxp.
(P.S., These messages are pretty tough to crack as written. I recommend attacking them with software helper tools if you know how to do two time pad puzzles. If you don't, noodle around for a bit about how you'd do it and maybe take a crack at the easier bits. Then make use of the hints I've supplied below, in ascending order of usefulness and cheatiness. As a benchmark, Lothar got about a quarter of each message translated in about half an hour before deciding software or mechanical help would be really nice for the rest. )
1. Basic method for two time pads -- match up the messages character for character, exactly. Guess a word. Given the format of the message, some are pretty easy to guess. Go down to the corresponding letters in the other message and rotate them by the same amount. Did you get garbage? You guessed wrong. Did it look reasonable? You guessed right. Use what you got to guess another word. (Start with the first three lines; those are easiest).
2. The first message concerns the activity and movement of a KGB agent on the west coast. The second contains information about resources for an agent in Argentina, and a further message for him. The messages aren't related.
3. The part of the second message you can't read says, \"_onspirative in his future work in Argentina.\"
4. The first message contains two Russian codewords: SHIRMANOV and SEVASTOPOL. (Don't worry, the rest is in English).
5. The first message contains the words 'steamship' and 'nothing'.
6. The fulltext of the first message can be found at nsa.gov/public_info/_files/venona/1944/5sep_soviet_sailed_from_portland.pdf .
In the 1940s, Soviet spies in the United States corresponded with Moscow using a cryptographic system known as a One Time Pad. OTP is literally the perfect code--completely unbreakable. Most codes are just \"excessively difficult, but with enough computers, it could be done\" unbreakable. OTP is literally unbreakable; if you follow its rules perfectly, then millenia from now, regaurdless of advances in cryptography and computing, a message you encode in OTP will still be unreadable.
The system is simple. You and your partner are equipped in advance with a pad of sheets of completely random numbers -- and these two pads are identical. When you need to send a message, you start by encoding your message in a standard cipher -- A=1, B=2, and so forth. You then take a sheet from your pad, and add the series random numbers to the message, doing all arithmetic mod 26. This you transmit, and your partner decrypts by using his copy of the sheet and subtracting off the random numbers. Then you both burn that sheet and never use it again. Thus \"One Time\" pad. (Actually, this is a simplification that isn't as secure--but it illustrates the point; for this exercise, it'll do).
Why is the \"one time\" part important? Well, it turns out that if you use the sequence twice, the messages are relatively easy to crack, though certainly harder than a symbol cipher. And as it historically turns out, the Soviets did exactly that. Their system was a little different than I described (they translated whole words to numbers instead of using a cipher), but it was perfectly secure from a cryptographic perspective. But apparently, Russian manufacturing being what it was, some of the pads were duplicated, and that means . . . used twice.
The United States's Project VENONA took advantage of the mistake, successfully decrypting many messages between KGB agents abroad and Moscow.
Can you solve the same problem?
The following two messages have been encoded with a Two Time Pad. It was supposed to be a One Time Pad, but the cipher was used twice. Of course, you won't be able to read the end of the longer message -- but if you're able to read any of either message at all, you'll know why. I've left the spaces and punctuation unchanged. The alphanumerics are rotated according to a series of random* numbers, arithemetic done mod 26.
* I used dice. So don't be tryin' to attack my pseudorandom number generator.
For fun, I've used messages actually decoded through Venona as the cleartext. In the 40's, this stuff was Top Secret.
---- First message ----
Uvxi: Xzj Lclbmhnmy
Mp: Chwxvr
5 Xyox., 1944
Lp Hqdohh,
KCVFGWXXN roubxa znfg Psginsxd sq wol sdgaxxnym IWABWLKGKB rn 31vl Dgxddf. Zu ael nnmrnys, fautprx ysb kphqk.
PGJS
---- Second message ----
Uvxi: Rnoizh
Hy: Ljxdxwywij
8 Zzun., 1944
Slwsq qt oau iprgneyw ge cdwtkcvzhg vtakslli frclr lgfzwk jeu ujoxja nebo flfdztn Ldkonn. Plqm Okpgmd ua ii gejdmvzabbjs bjwskdehcxod fm use qhvfxy scmq am Jwqguskxp.
(P.S., These messages are pretty tough to crack as written. I recommend attacking them with software helper tools if you know how to do two time pad puzzles. If you don't, noodle around for a bit about how you'd do it and maybe take a crack at the easier bits. Then make use of the hints I've supplied below, in ascending order of usefulness and cheatiness. As a benchmark, Lothar got about a quarter of each message translated in about half an hour before deciding software or mechanical help would be really nice for the rest. )
1. Basic method for two time pads -- match up the messages character for character, exactly. Guess a word. Given the format of the message, some are pretty easy to guess. Go down to the corresponding letters in the other message and rotate them by the same amount. Did you get garbage? You guessed wrong. Did it look reasonable? You guessed right. Use what you got to guess another word. (Start with the first three lines; those are easiest).
2. The first message concerns the activity and movement of a KGB agent on the west coast. The second contains information about resources for an agent in Argentina, and a further message for him. The messages aren't related.
3. The part of the second message you can't read says, \"_onspirative in his future work in Argentina.\"
4. The first message contains two Russian codewords: SHIRMANOV and SEVASTOPOL. (Don't worry, the rest is in English).
5. The first message contains the words 'steamship' and 'nothing'.
6. The fulltext of the first message can be found at nsa.gov/public_info/_files/venona/1944/5sep_soviet_sailed_from_portland.pdf .
I have a couple cryptographic questions:
1. Drak, how was the coordination done to make sure that the proper sheet of the pad was used?
2. My dad thought of a way of encode things, and I can't think of problems that might be associated. Here's the premise, anyone wanna poke holes in it?
Use a substitution-based method, on a word by word basis. Substitute based on a number of substitution index books. These books would be randomly-picked (and probably long) works of literature. Additionally, you could have a matched set of books with completely random words.
To encode, you do a word-search for the word you want, and substitute it with an index of the location of the word. The index should be something like book#, page#, word#, or something of the sort that will make the books publisher-specific. The library would be exhaustive enough that multiple instances of practically any word would exist, and repeated use of any index would be disallowed. You could use a combination of varied vocabulary and the rotation of books in & out of use to avoid repetition of and index.
So, how strong and/or weak would this system be? Why?
1. Drak, how was the coordination done to make sure that the proper sheet of the pad was used?
2. My dad thought of a way of encode things, and I can't think of problems that might be associated. Here's the premise, anyone wanna poke holes in it?
Use a substitution-based method, on a word by word basis. Substitute based on a number of substitution index books. These books would be randomly-picked (and probably long) works of literature. Additionally, you could have a matched set of books with completely random words.
To encode, you do a word-search for the word you want, and substitute it with an index of the location of the word. The index should be something like book#, page#, word#, or something of the sort that will make the books publisher-specific. The library would be exhaustive enough that multiple instances of practically any word would exist, and repeated use of any index would be disallowed. You could use a combination of varied vocabulary and the rotation of books in & out of use to avoid repetition of and index.
So, how strong and/or weak would this system be? Why?
- Kilarin
- DBB Fleet Admiral

- Posts: 2403
- Joined: Wed Aug 07, 2002 2:01 am
- Location: South of Ft. Worth Texas
It's one variation of a Book CipherSnoopy wrote: Substitute based on a number of substitution index books.
They are interesting codes, and have been used frequently in reality. BUT, the enemy usually figures out the source eventually.
Check out the first part of the Beale ciphers for another example.
For anyone working on the cool two time pad problem, you might want to check out this thread on a cryptography forum I sometimes frequent:
http://s13.zetaboards.com/Crypto/topic/123691/1/
Some very BASIC hints on two time pads: (I may be duplicating information Drakona has already provided in her hints)
Highlight from here:
The reason using a one time pad twice destroys it's security is that it eliminates the key.
For example, lets assume our one time pad key was the letters AGYJG and we were encrypting the word "HOUSE" the result would be:
H+A=8+1=9 =I
O+G=15+7=22 =V
U+Y=21+25=46 MOD 26=20 =T
S+J=19+10=29 MOD 26=3 =C
E+M=5+13=18 =R
so HOUSE encrypts to IVTCR
BUT, now we encrypt CLAMS using the SAME key:
C+A=3+1=4 =D
L+G=12+7=19 =S
A+Y=1+25=26 =Z
M+J=13+10=23 =W
S+M=19+13=32 MOD 26=6 =F
So CLAMS encrypts to DSZWF
BUT, now we know an interesting thing. Lets look at just the first letter of both words.
H+A=I C+A=D
If we SUBTRACT them, we get something interesting.
I-D= H+A-C-A = H-C
Since they were both encrypted with the same key letter (A) we can ELIMINATE that letter from the formula entirely by subtraction. If we do this with the entire message, we now end up with two messages that are STILL encrypted, but instead of with a random key, each message is encrypted with the other message! (this is even EASIER when the encryption was done with XOR)
It is impossible, of course, to guess a true random key. But it is VERY possible to figure out the words of two real messages encrypted with each other. In Drakona's excellent challenge, note the format. It suggest some contents of both messages immediatly. And if you know part of message 1, you can now use that to decrypt the corresponding part of message 2! And that may be enough to guess another word or two of message 2, which can be put right back into message 1 to get more of it. It's a processes that feeds off of itself.
Another attack you should be trying is the "Probable word drag". For example, if you think the word "GENERAL" was likely to occur in message 1, you can drag it through all of message 2. Anywhere that GENERAL is NOT really the content of message 1, you will get garbage when using it to decrypt message 2. BUT, as soon as you hit the RIGHT spot, the place where the word actually occurs in message 1, message 2 will decrypt into something that makes sense. Thereby giving you another part of both messages!
---to here
Anyway, good luck to everyone! I hope to get some time to work on this myself tonight!
Re:
You know it was because of you I started playing Eve. Still am. So can you sneak me a Polaris frig to fly.Valin Halcyon wrote:Yes, the Ghost of Christmas Past or some such...
Nope, not a part of..whatever you said. Just a programmer. I work for CCP Games on EVE Online now.
This is my non-expert analysis:snoopy wrote:So, how strong and/or weak would this system be? Why?
Even if you assume that the attacker can't guess the book that you used (i.e. maybe it is an original work that only you and one other person have), it still wouldn't give you perfect secrecy. Consider the worst case of when you index two words that are right next to each other in the book. Some words are statistically more likely to follow other words in the English language, so this would give an attacker some information about your message. The same can be said for a word pair separated by one word, separated by two words, and so on, but of decreasing statistical usefulness. You wouldn't have to limit the analysis to just word pairs, but you could also analyze the distribution of any n-tuple of words. Still, as words being indexed become increasingly separated, this will become decreasingly useful. Another problem may be when indexing the first few words of the book or the last. I think that you could perform the same sort of statistical analysis of what sort of words typically begin sentences. But I don't know if these weaknesses could be used, in practice, to crack such a message, especially if you are smart about not indexing words that are near each other in the book.
If you are using published books though, an attacker with an electronic database of books could just try brute forcing every book seeing which ones yield a grammatical decrypted message.
I think that an improved approach would be to just reduce the encryption to a one time pad, except on the word level: Exchange dictionaries of, say, 1,000 words and sheets of random numbers between 0 and 999, inclusive. Then do as before when creating the encrypted message with letters except now by using words, taking the sum of each word's index in the dictionary and the corresponding number on the pad mod 1,000.
Re:
I don't know. I've always figured it was indicated in cleartext at the top, and Moscow had a book of them. Seems the most practical thing to do, and you don't really sacrifice any security.snoopy wrote:I have a couple cryptographic questions:
1. Drak, how was the coordination done to make sure that the proper sheet of the pad was used?
Given that Venona had to solve the code as well as the one time pad, I don't see how they could have done it any other way. And plus, they seemed to sometimes know that a message was 'solveable' without having been able to solve it, which indicates to me they had a way to match them up.
But I've actually never seen what the ciphertext messages from Venona looked like, or read a really solid technical description of what happened. I've always wondered about details like that.
Not very strong. Here's how I'd crack it. I'd take all of your messages and look for a the smallest number of books that generated the most adjacent words. For example, if you used books 5 1 4 2 3 2 4 5 3 2 2, I'd take a crack at books 3 and 2. Next, I'd set up a computer program to look up the words/pages based on an arbitrary book. I would then brute force through the library to see what "2 3 2" and "3 2 2" gave me with any two books in existence. I'd run that through a 'probable English phrases' algorithm and then a wetware filter. Once I had a couple books nailed down, I'd work outward at the edges.Snoopy wrote: 2. My dad thought of a way of encode things, and I can't think of problems that might be associated. Here's the premise, anyone wanna poke holes in it?
. . .
So, how strong and/or weak would this system be? Why?
Or if you want to defend against that and never repeat books, you're basically just using a codebook. In which case, either the size of your library seriously limits how many messages you can send, or you wind up vulnerable to some kind of frequency analysis. And it has all the drawbacks of codebooks in terms of captured materials.
When it comes to cryptography, you're best off with well-known software based on well-known algorithms in the open literature. I'll take proof (or at least professional review) over obscurity any day.
Re:
Seriously. That sort of thinking leads to just getting a concealed carry permit instead of studying martial arts for 20 years.Kilarin wrote:Very efficient, but no fun to crack.ccb056 wrote:I'll stick with my 4096 bit public key-private key aes encryption.
sorry for the necro, but this just hit me.
Valin: you should definitely try your hands at this: http://en.wikipedia.org/wiki/Voynich_manuscript

Valin: you should definitely try your hands at this: http://en.wikipedia.org/wiki/Voynich_manuscript